Best Practices of Application Security Assessment
Businesses are continuously striving to minimize risks of cyberthreats by strengthening their infosecurity, aligning with the international standards and regulations, introducing strict NDA’s, and following the security-by-design concept.
As developers, we understand how essential it is to use tools that are 100% secure in your work. We make every effort to ensure scam-proofness and reliability of our solutions. The case of Log4Shell vulnerability that impacted over 35,000 Java packages globally has proven once again that security of apps and solutions is a top priority that must be continuously and strictly monitored.
Infopulse has been working on the new product for application packaging workflow management PACE Packager Hub released in January 2021. The solution was developed with a view to modern standards and best security practices and successfully passed the Application Security Assessment.
We’ve had a consistent talk with the representatives of the security department of Infopulse that have been working on PACE Packager Hub as well as on many digital solutions over the previous decades. We’ve asked the infosec team about the main stages of security checks, methodologies used for security testing of applications, and recommendations for application users to keep their sensitive data as safe as possible.
Nowadays, a large part of life has seamlessly migrated into apps and services in our pockets, which we use in our daily activities. These apps require pretty much personal and financial information from users, and every single piece of this data must be secured. What are the major requirements to the security of the solution?
The application must provide three major concepts of application security – CIA: Confidentiality, Integrity, and Availability – these are the main requirements to the security of the solution.
What are the main modern best practices in the field of information security?
We say that the one and only entirely secure app is the one not connected to any network and installed on a computer that is turned off (laughs). Meaning that not a single solution people are using can be stated to be 100% secure. The only way to prevent breaches is to run regular consistent security checks, discover and fix vulnerabilities before they are discovered by somebody else.
So, we can name the following three basic practices in the field of infosec:
- Secure connections;
- Minimization of application exposure to the public networks;
- Strength of business logic of the application.
What criteria are usually checked during the security assessment?
When conducting the security assessment, we check the following categories according to the OWASP TOP-10 2021:
- Broken Access Control
- Cryptographic Failures
- Sensitive Data Exposure
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery
We keep hands at the pulse of security requirements and conduct regular checks regarding the most widespread vulnerabilities.
What is the average duration of a typical security check?
Average duration of a typical security check depends on the size of the application we’re testing. If the app is simple, the security assessment takes about 40 hours. If the application has a database and API component in its structure, then security check may take about 80 hours. If the application is distributed or is micro-segmented, it will take even more time.
Can you name the main stages of such a security assessment?
Sure, they are standard for all applications:
- Collecting information about the app (Passive information gathering to get as much information as possible that is publicly available without establishing any contact between yourself and the target, such as public IP addresses, subdomains, directory indexes, passwords and usernames, publicly available sensitive documents and files, etc.)
- Reconnaissance of the app (Active information gathering to find as much data as you can establishing a contact with the target: open ports on applications, IP address ranges, app versions and platforms, technologies used, API keys, etc.)
- Vulnerability scanning of the app itself If the software is found vulnerable, then we do the Vulnerability Assessment of the app.
- Report
We know that your team was involved in the development of PACE Packager Hub, a workflow solution for application packaging teams. What approach have you used for the secure development of this application?
We have adopted the concept of the Security-by-design (SBD) regarding all our projects, PACE Packager Hub is no exception. This approach means that we address security issues of the software already during the R&D and design phases.
The build of PACE Packager Hub was developed according to DevSecOps strategy – security requirements were created for an App during the stage of its planning. Each module was checked consequently after each step of development, and all the findings were fixed.
What was checked during the latest security assessment of PACE Packager Hub?
During PACE Packager Hub’s security assessment, we’ve checked the following:
- Ports the app uses;
- Services that are running on these ports;
- The version of services which are used and if they are vulnerable.
If yes, the following vulnerabilities are checked:
- Web component of the application for XSS, SQL Injections, CSRF, and other web vulnerabilities;
- The API component according to the best practices.
What security assessment tools did you use during the assessment of PACE Packager Hub?
For vulnerability scanning we used a few different tools to avoid false positive (negative) assessments:
- Metasploit Framework
- Nexpose Community Edition
Website testing was performed using such tools as Acuentix and BurpSuite Pro. Tests were performed with three access levels: customer, engineer, and supervisor.
We have also used the following tools:
- Nmap (port scanner)
- Postman (API tool)
- Custom scripts for various activities (brute forcing, fuzzing, etc).
Did you use specific security standards and frameworks during the assessment of PACE Packager Hub?
During the assessment of PACE Packager Hub, we used the combination of various frameworks and best practices:
- Security Assessment: the Penetration Testing Execution Standard (PTES), OWASP Testing Guide, USA NIST 800-115, Offensive Security Certified Professional (OSCP) best practices, EC-Council Security Assessment methodology, ISF SoGP, and CIS Controls.
- Risk assessment and risk management: ISO 27000 standards series, specifically ISO 27005.
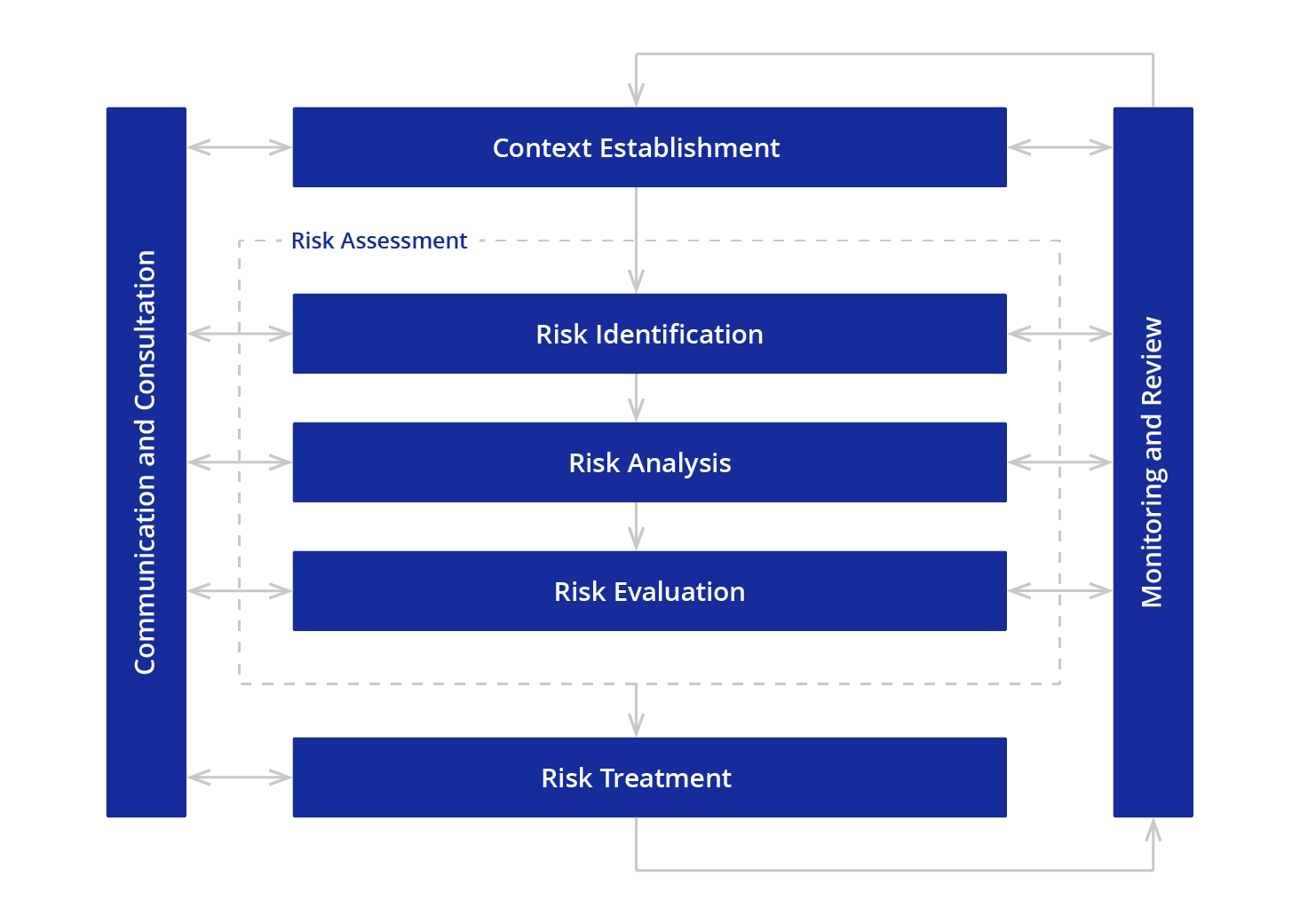
What security assessment and risk management methods did you follow?
In the security check of PACE Packager Hub, we used the CRAMM-based risk analysis methodology according to the recommendations of the British Standards Institution.
We have assessed two parameters for each security threat and vulnerability to define the risk value: Impact, indicating the possible outcome for the app in case of an attack (low – critical) and likelihood, reflecting the probability of the incident reproduction in a real environment (low – very high).
Then we have identified the most serious risks in the Risk Registry, a key security document, which should be supported, updated and used during the solution life cycle, planning and implementation of new releases and solution support.
What are the results of the assessment of PACE Packager Hub?
We can say that it exposes only the minimum required number of ports in use. PACE Packager Hub complies with modern best practices in the field of information security and minimizes both the attack surface and the likelihood of compromising the data contained in it.
Can you name some security tips for the users when working with PACE Packager Hub?
Every solution has the best recommendations to make its usage more secure. With PACE Packager Hub, these recommendations are as following;
- Install SSL Certificate;
- Minimize the number of Apps on the Server, where the Product is installed. Use only NEEDED apps;
- Update all the components in a timely manner.
We also added additional post-test recommendations to the User Guide, so it includes the most critical tips as for the moment of its writing.
Final word
There’s no secret magic pill to ensure 100% security of any software. However, adhering to the best security practices, adopting the security-by-design approach, and regular application security audits are some of the methods of minimization of the data breach occurrences.
Keeping in mind that cybersecurity remains a major threat today, organizations should strive to reduce vulnerabilities of the solutions they are developing. Consistent and continuous improvements of security measures and training of users to work with the apps in the right way are among the main preventive steps to potential hazards.










