Note
You are not reading the most recent version of this documentation. See the latest version available.
Server Installation (for production purposes)¶
Install the server part of the PACE Packager Hub solution on the on-premise server within the company infrastructure.
For information, see Hosting Options
Warning
Before installation check/install the Server-side Prerequisites
- Run the downloaded PACE Packager Hub - Server installer.

- Click Next.
- Read and accept the END USER LICENSE AGREEMENT and then click Next.
- Leave the default installation location or choose an alternative one and click Next.
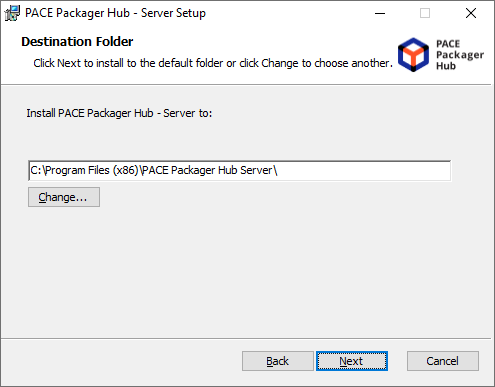
- Select the For production installation mode and click Next.
The installation will ask you to manually specify the SQL database connection credentials and select the Web Server.
- Enter the Microsoft SQL Server connection credentials and a name of the database, created for PACE Packager Hub. Then, click Next. The installation will check the connection to the specified database.
Note
If you are using Microsoft SQL Express, installed locally, specify the server address in format:
localhost\sqlexpress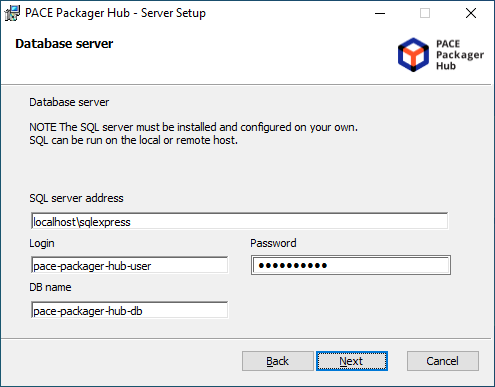
- Choose the IIS or Kestrel Web Server. For IIS, enter a Site name that will be automatically created and configured on the server by the installation. Also, set the Binding IP address and Binding port for PACE Packager Hub site on the web server. Then, click Next.
Note
IIS Web Server must be enabled manually. See Server-side PrerequisitesKestrel Web Server is included in the installation and will be run automatically.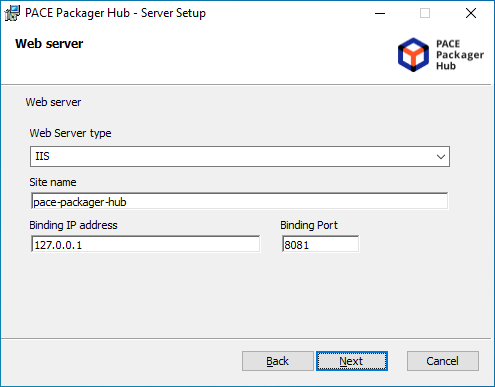
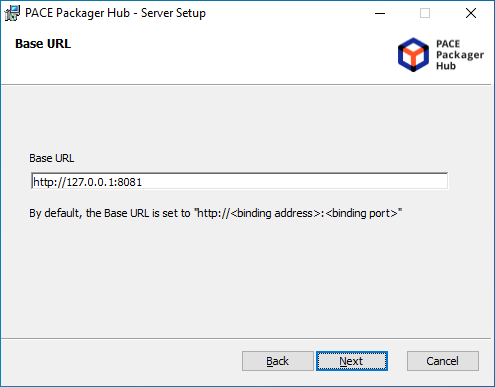
- Specify the Base URL of the system. This is the address at which the system is available to users. The specified base URL is also used as an ‘Issuer’ of authorization token and as a part of URL to order/package in email notifications.
You can later change the defined Base URL in the system settings of PACE Packager Hub.
- Click Install.
- Wait until the installation is completed.
- Click Finish to close the installation.
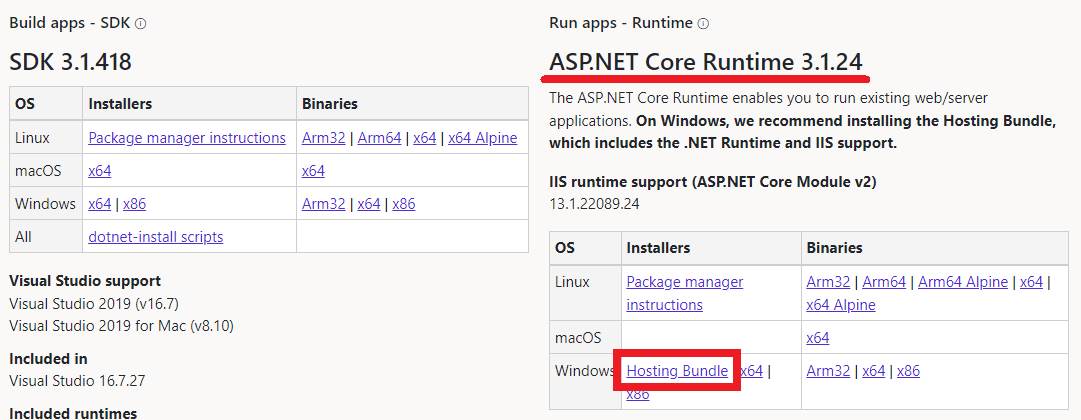
- If you have selected IIS Web Server, install post-requisite ASP.NET Core Runtime 3.1.10 or higher.
Note
Please ensure that you are downloading and installing the Hosting Bundle.
- Access PACE Packager Hub at http://127.0.0.1:8081 using your Web Browser.
Warning
Before start using PACE Packager Hub for production purposes, consider configuring your Web Server as described below in this instruction.
Note
We recommend using browser listed in Supported Browsers
Default login credentials:Email:supervisor@company.comPassword:12345
Web Server configuration¶
Consider configuring your Web Server to minimizes both the surface of the attack and the likelihood of compromising the data.
- HTTPSConfigure transport-level encryption (TLS v1.2 - 1.3) to protect all communications passing between the Web Browser, Desktop App and the Web Server.Also, use HSTS header with SSL to avoid SSL Strip attack.For configuring Kestrel Web Server edit appsettings.json file, located at
"C:\Program Files (x86)\PACE Packager Hub Server"For information, see Endpoint configuration.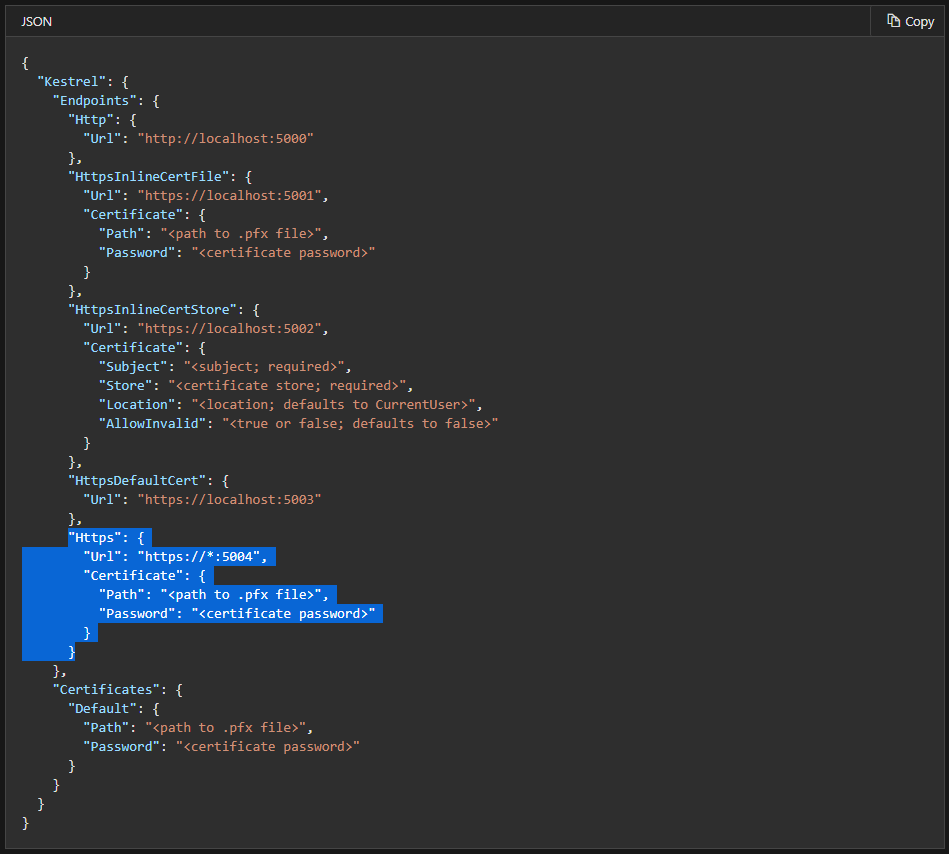
- Hide software versionThe server software versions used by the application are revealed by the web server. Displaying version information of software information could allow an attacker to determine which vulnerabilities are present in the software, particularly if an outdated software version is in use with published vulnerabilities.
- Server:
Microsoft-HTTPAPI/2.0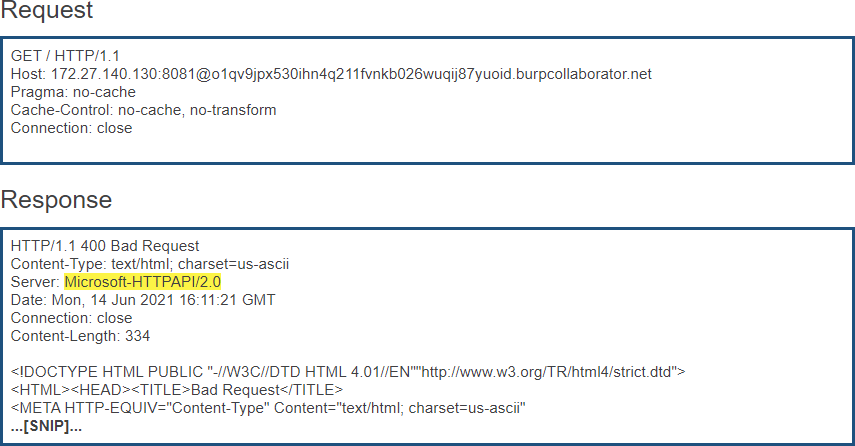
- Server:
Microsoft-IIS/10.0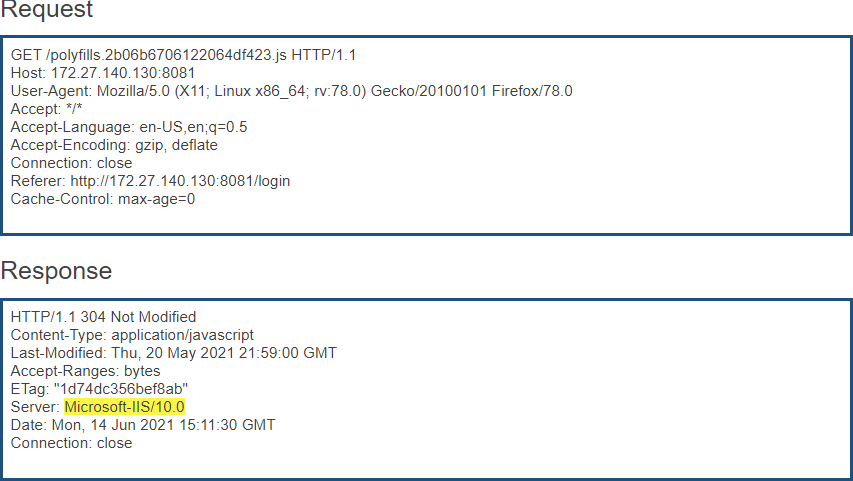
- Set the X-XSS-Protection header
Set the
X-XSS-Protection: 1; mode=blockheader either for PACE Packager Hub site or whole Web Server.Issue background: Cross-site scripting (XSS) filters in browsers check if the URL contains possible harmful XSS payloads and if they are reflected in the response page. If such a condition is recognized, the injected code is changed in a way, that it is not executed anymore to prevent a successful XSS attack. The downside of these filters is, that the browser has no possibility to distinguish between code fragments which were reflected by a vulnerable web application in an XSS attack and these which are already present on the page. In the past, these filters were used by attackers to deactivate JavaScript code on the attacked web page. Sometimes the XSS filters itself are vulnerable in a way, that web applications which were protected properly against XSS attacks became vulnerable under certain conditions. - Set the X-Frame-Options header
Set the
X-Frame-Options: DENYheader either for PACE Packager Hub site or whole Web Server.Issue description: If a page fails to set an appropriate X-Frame-Options or Content-Security-Policy HTTP header, it might be possible for a page controlled by an attacker to load it within an iframe. This may enable a clickjacking attack, in which the attacker’s page overlays the target application’s interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions.Note that some applications attempt to prevent these attacks from within the HTML page itself, using “framebusting” code. However, this type of defense is normally ineffective and can usually be circumvented by a skilled attacker. - Limit requests
Consider setting limits on HTTP requests that are processed by the Web server to avoid DDoS / brute-force attacks.
- Set Issuer in authentication token
Set the
Issuerparameter to the public site name in the appsettings.json (at"C:\Program Files (x86)\PACE Packager Hub Server"). TheIssueris used and checked in the authentication token.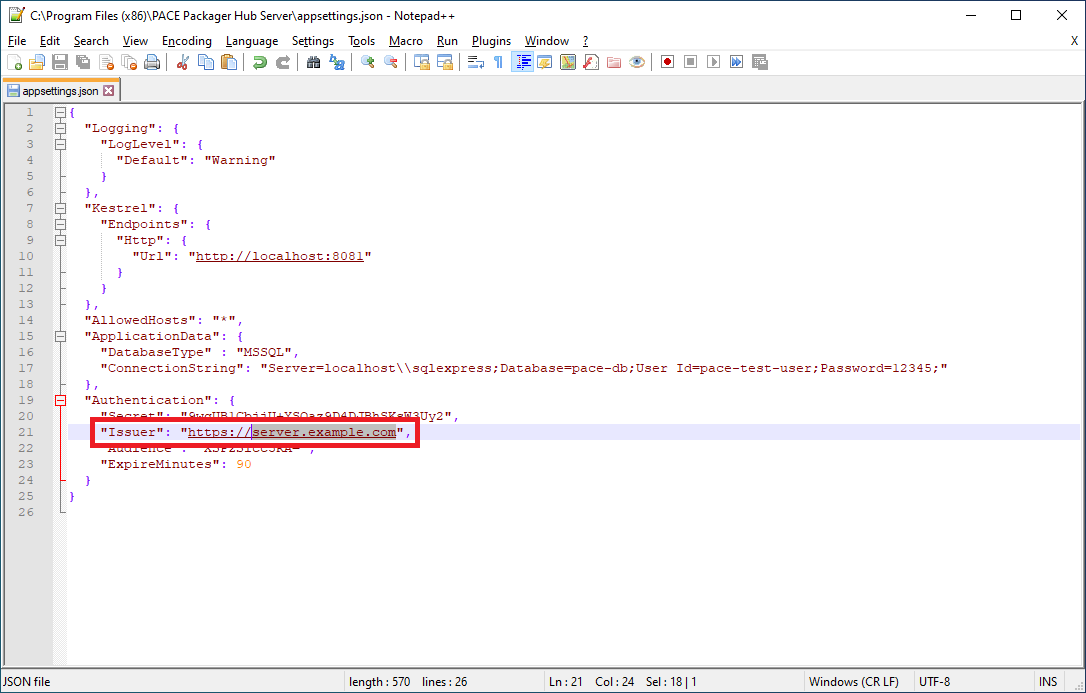
- Increase IIS max file size for upload
If you are using IIS Web Server and experiencing issues with uploading big files to PACE Packager Hub, consider changing the maximum allowed size of a file that can be uploaded. By default, this parameter is set to 28.6 MB. Set a new limit in the
maxAllowedContentLengthattribute of the requestLimits element
Note
PACE Packager Hub PACE Packager Hub is an end-to-end ecosystem that is fully dedicated to customer servicing, teamwork, and management of packaging tasks in teams of any size - learn more.
Try PACE Packager Hub for free - 21 days no obligations unlimited trial with all functions unlocked.
